
Items of practical training certificates Cisco CCNP_BCMSN (Building Cisco Multilayer Switched Networks)
Start practicing: Configuring a Distribution Switch

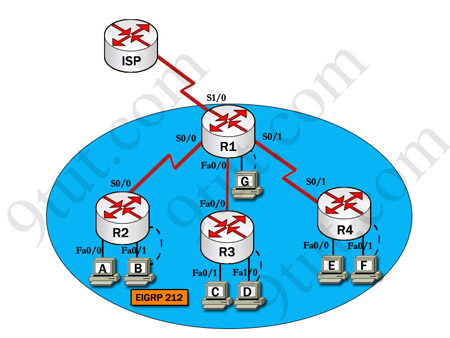
| R1 Fa0/0: 192.168.77.33 S1/0: 198.0.18.6 S0/1: 192.160.60.25 | R2 Fa0/0: 192.168.60.97 Fa0/1: 192.168.60.113 S0/0: 192.168.36.14 |
| R3 Fa0/0: 192.168.77.34 Fa0/1: 192.168.60.65 Fa1/0: 192.168.60.81 | R4 Fa0/0: 192.168.60.129 Fa0/1: 192.168.60.145 S0/1: 192.168.60.26 |


1 A PC can not connect to any remote websites, ping its default gateway, or ping a printer that is functioning properly on the local network segment. Which action will verify that the TCP/IP stack is functioning correctly on this PC?
Use the ipconfig /all command at the host?s command prompt.
X Use the ping 127.0.0.1 command at the command prompt.
Use the traceroute command at the command prompt to identify any failures on the path to the gateway.
Use FTP to check for connectivity to remote sites.
Download a troubleshooting tool from the PC manufacturer's website.
2 Refer to the exhibit. Which set of devices contains only intermediary devices?
X A, B, D, G
A, B, E, F
C, D, G, I
G, H, I, J
3 Refer to the exhibit. When computer A sends a frame to computer D, what computers receive the frame?
X only computer D
only computer A and computer D
only computer B, computer C, and computer D
all computers